
On May 10, 2023, the National Institute of Standards and Technology (“NIST”) released an Initial Public Draft of Revision 3 to NIST Special Publication (“SP”) 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations. Although still in draft form, the document provides important guidance to federal government contractors and other companies that must use NIST SP 800-171 as a baseline for cybersecurity compliance. The draft Revision 3 was informed by public comments received by NIST, and NIST is seeking additional public comment on this revision.
Background
NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems. SP 800-171 is used as a baseline of security requirements for protection of controlled unclassified information (“CUI”)—sensitive information that requires certain confidentiality, access, or dissemination controls—when that information resides outside of federal government systems (i.e., on contractor systems). The requirements apply to those components of nonfederal systems that process, store, or transmit CUI or that provide protection for such components, and only where no other applicable law, regulation, or policy prescribes different or more specific safeguarding requirements. The NIST SP 800-171 requirements are imposed via contractual vehicles or other agreements established between federal agencies and nonfederal organizations. Outside of government agreements, commercial parties also may require or rely upon the requirements of NIST SP 800-171 as a cybersecurity compliance standard.
The requirements of SP 800-171 are derived from Federal Information Processing Standards (“FIPS”) 199, Standards for Security Categorization of Federal Information and Information Systems; FIPS 200, Minimum Security Requirements for Federal Information and Information Systems; and NIST SP 800-53, Security and Privacy Controls for Federal Information Systems and Organizations. For purposes of CUI protection under NIST SP 800-171, NIST has assumed that the confidentiality impact value for CUI is no less than moderate under the FIPS categorization methodology. To develop the NIST SP 800-171 controls, NIST started with the more rigorous NIST SP 800-53 controls for a moderate control baseline, which satisfy the minimum security requirements under FIPS 200. It then tailored those controls to eliminate those that are: (i) primarily the responsibility of the federal government; (ii) not directly related to protecting the confidentiality of CUI; or (iii) expected to be implemented by organizations without specification by the federal government.
The NIST SP 800-171 security requirements are a subset of controls necessary for an information security program. Under Revision 2, 14 control families were present; but with Revision 3, they are organized into 17 control “families,” as follows:
Access Control | Maintenance | Security Assessment and Monitoring |
Awareness and Training | Media Protection | System and Communications Protection |
Audit and Accountability | Personnel Security | System and Information Integrity |
Configuration Management | Physical Protection | Planning* |
Identification and Authentication | Risk Assessment | System and Services Acquisition* |
Incident Response | Supply Chain Risk Management* |
Families with an asterisk (*) have been added with Revision 3 to maintain consistency with the NIST SP 800-53B moderate control baseline.
Section 3 of NIST SP 800-171 describes applicable requirements for each of these control families, including numerous subcategories of requirements within each family. For each subcategory, there is a discussion section, with examples, as well as references to source controls from NIST SP 800-53 and a list of supporting publications. As discussed below, one of the proposed changes with Revision 3 is the addition of organization-defined parameters (“ODP”), which allow for additional flexibility for federal agencies by permitting them to set specific values for defined parameters. Once specified, these ODP become part of the requirement.
Proposed Changes Introduced Through NIST SP 800-171, rev. 3
In the draft Revision 3, NIST has proposed several significant changes from the prior version of the publication. The updates are designed to streamline and clarify requirements. Below, we highlight some of the most consequential modifications.
Elimination of the distinction between basic and derived security requirements
NIST has proposed to eliminate the distinction between basic security requirements from FIPS 200 and derived requirements from NIST SP 800-53. NIST SP 800-171 previously required compliance with both basic and derived controls, but the revision now proposes to require compliance only with derived controls. This is due in part to NIST’s recognition that FIPS 200 requirements are very high-level and lack sufficient specificity to be useful.
Updating of security controls
NIST has proposed to streamline security requirements by removing outdated and redundant requirements. It has also added new security requirements, thus keeping the number of security controls approximately the same.
Increase in specificity of security requirements
NIST has proposed to increase the level of detail of the various security requirements in order to remove ambiguity, improve effective implementation, and clarify the scope of assessments. This was likely in reaction to feedback that previous requirements were open to interpretation, which has made compliance and security assessments more challenging. Introducing specificity has the potential to make compliance with specific controls more onerous by reducing organizational flexibility with respect to protecting CUI, but it also may facilitate compliance by clarifying security requirements.
Update of security requirements to reflect recent changes in NIST SP 800-53 and SP 800‑53B
NIST has updated the security requirements and families in NIST SP 800-171 to reflect updates in, and better align with, NIST SP 800-53, rev. 5 and NIST SP 800-53B, Control Baselines for Information Systems and Organizations. This was in response to feedback that organizations are overwhelmed by the number of potentially applicable security and risk management frameworks for the public and private sectors. To facilitate the harmonization of requirements, NIST has provided as part of the revision a Prototype CUI Overlay, which shows how the moderate control baseline in NIST SP 800-53B can be tailored at the control and control‑item levels to align with the NIST SP 800-171 security requirements.
Introduction of ODP
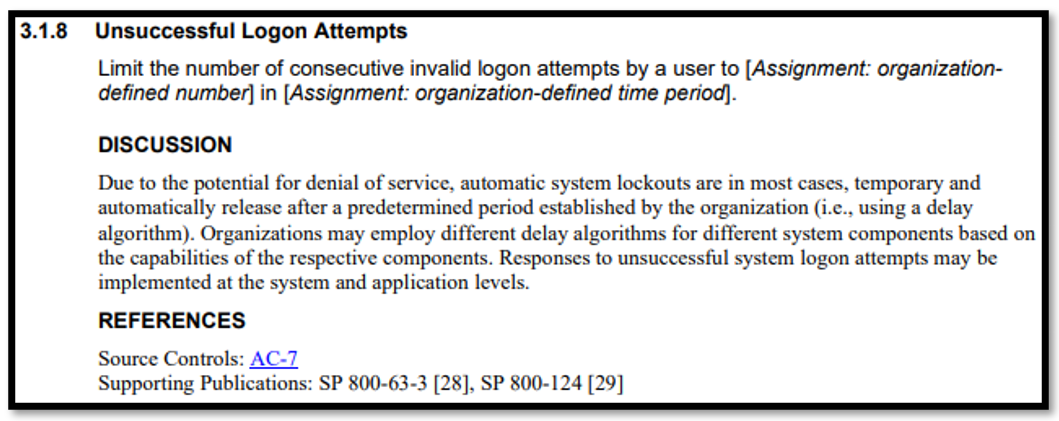
As noted above, another significant proposal is the introduction of ODP for certain security requirements. ODP currently are present in NIST SP 800-53 to provide government agencies with flexibility to tailor security requirements to their specific needs. NIST is now proposing to introduce ODP to NIST SP 800-171 to give federal agencies similar flexibility to tailor requirements for protection of CUI. ODP would be reflected in NIST SP 800-171 through agency‑assigned parameters such as time periods and numbers of operations, as shown in the example below:
View a detailed analysis of the updates from Revision 2 to Revision 3.
Next Steps
Public comments on the Initial Public Draft should be submitted to NIST by July 14, 2023. NIST has indicated that it is specifically interested in feedback related to re-categorized controls, ODP, and the Prototype CUI Overlay. See a template for comments.
In the meantime, federal contractors and others who are bound by the NIST SP 800‑171 requirements should review the updated revision and associated materials and prepare to adjust their security controls and systems at such time as the newly revised publication is adopted by their customers. We recommend particular focus on the three new control families and their requirements.
In terms of timing, contractors should bear in mind that Revision 3 generally will not require regulatory changes and may be implemented through contract modifications. For example, the applicable Defense Federal Acquisition Regulation Supplement (“DFARS”) clause requires compliance with the version of NIST SP 800-171 “in effect at the time the solicitation is issued or as authorized by the Contracting Officer.” DFARS 252.204-7012(b)(2)(i). Similarly, we have seen the Department of Veterans Affairs include language in certain contracts that commits the parties to agree to negotiate in good faith the implementation of updated security requirements in FIPS or NIST SPs after contract execution. In other words, Revision 3 not only will begin to be required as soon as it moves from draft to final publication in all new procurements, but also may be adopted for existing contracts through contract modifications.
Even for those companies not involved in federal contracting, changes to NIST security requirements very often are adopted by industry more broadly as best practices, so these updates should also be carefully considered by the private sector more broadly.